Do We Think Chocolate Guy Is Gay?
do we think chocolate guy is gay?
More Posts from Silentj1018 and Others

Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from no-reply@accounts.google.com This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
Hey, look at me. Look at me. I’ve said it once and I’ll say it again: you need to condition yourself to being okay with being inconvenienced by things. The first time I spoke about this I meant it in a mental health way- it is good to go out to the store and see people versus just ordering alone at home- but there is another more pressing societal issue you should be more concerned about as well.
Any service you rely on for convenience can be weaponized against you the moment you begin to rely on it. Streaming used to be a cheap and convenient way to see movies at home. It is now exorbitantly expensive, you need multiple accounts just to get what you want, and any of those movies can be taken from you at any time. And unless you have gotten used to going through the “inconvenience” of owning physical media, you can do nothing about it. Same goes for buying things on Amazon. Same goes for any service like DoorDash etc. These companies WANT you to be reliant on them for convenience so they can do whatever they want to you because, well, what else are you gonna do?
Same thing goes for the uptick in AI. If you train yourself to become reliant on AI for doing basic things, you will be taken advantage of. It is only a matter of a couple years before there are no free AI services. Not only that, but in the usage of AI’s case, it is robbing you of valuable skills that you need to curate that you will be helpless without the moment the AI companies drive in the knife the way they have done with streaming. Delivery. Cable. Internet. Etc. It will happen to AI too. And if you are not practicing skills such as. Writing. You are not only going to be at the mercy of AI companies in the digital world, but you are going to be extremely easy to take advantage of in real life too.
I am begging you to let go of learned helplessness. I am begging you to stop letting these companies TEACH you helplessness. Do something like learn to pirate. It is way more inconvenient at the beginning, but once you know how, it is one less way companies can take advantage of you. Garden. Go to the thrift store (older clothes hold up better anyway). These things take more time and effort, yes, but using time and effort are muscles you need to stretch to keep yourself from being flattened under the weight of our capitalist hellscape.
Inconvenience yourself. Please. Start with only the ways you are able. Do a little bit at a time. But do something.

when she says she doesn’t send nudes


So I ended up with free time at the end of my first class today, so I was like "do yall wanna see a vintage meme?" and turned on "what does the fox say". Expected like. A laugh from the kids, or even just a "wtf is this mx?" which is. A reasonable reaction to What Does The Fox Say.
But instead of a reasonable reaction. all of my students watched the first 60 seconds with jaws agape. And then this one kids turns to me like the fucking eye of Sauron and literally goes:














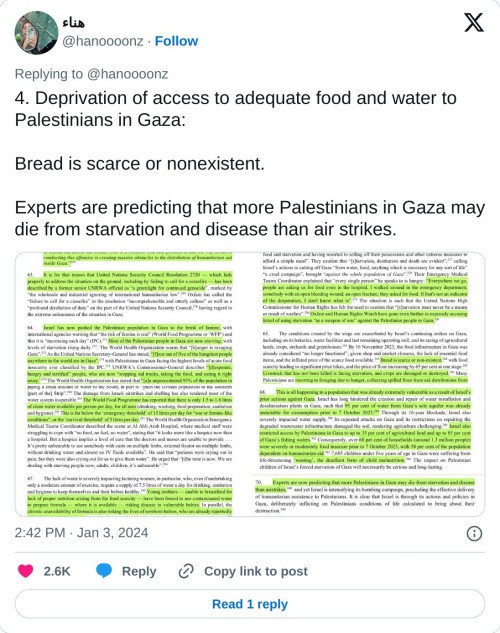
















You can read the rest of the thread here. Plus here's the 84 page document submitted by South Africa

(Source)
WOW
This I think is unprecedented, holy shit. All the original characters from Fables and its spinoffs are public domain now!!
Man this one is from way back enough that I knew it completely divorced from the concept of reaction images/clips for YEARS
First time I saw it was absent any other context, just "hey check out this funny little video"
just saw this clip and i think itd make a funny reaction image what do u think... does it have potential
-
 cordi-b-world liked this · 2 weeks ago
cordi-b-world liked this · 2 weeks ago -
 solecyinglife reblogged this · 2 weeks ago
solecyinglife reblogged this · 2 weeks ago -
 arkgoz liked this · 2 weeks ago
arkgoz liked this · 2 weeks ago -
 unaskedwhale reblogged this · 2 weeks ago
unaskedwhale reblogged this · 2 weeks ago -
 alice-jpeg reblogged this · 2 weeks ago
alice-jpeg reblogged this · 2 weeks ago -
 alice-jpeg liked this · 2 weeks ago
alice-jpeg liked this · 2 weeks ago -
 captainkastyn reblogged this · 2 weeks ago
captainkastyn reblogged this · 2 weeks ago -
 badass-ballerina liked this · 2 weeks ago
badass-ballerina liked this · 2 weeks ago -
 vampnoise liked this · 2 weeks ago
vampnoise liked this · 2 weeks ago -
 localdorkincombatboots reblogged this · 2 weeks ago
localdorkincombatboots reblogged this · 2 weeks ago -
 deterioratingpisces liked this · 2 weeks ago
deterioratingpisces liked this · 2 weeks ago -
 imppie liked this · 2 weeks ago
imppie liked this · 2 weeks ago -
 seasonedholidayham liked this · 2 weeks ago
seasonedholidayham liked this · 2 weeks ago -
 seasonedholidayham reblogged this · 2 weeks ago
seasonedholidayham reblogged this · 2 weeks ago -
 batsintheshadows reblogged this · 2 weeks ago
batsintheshadows reblogged this · 2 weeks ago -
 cursedberrycompote reblogged this · 2 weeks ago
cursedberrycompote reblogged this · 2 weeks ago -
 instrumomentum reblogged this · 2 weeks ago
instrumomentum reblogged this · 2 weeks ago -
 instrumomentum liked this · 2 weeks ago
instrumomentum liked this · 2 weeks ago -
 matthew-the-imp-of-the-perverse reblogged this · 2 weeks ago
matthew-the-imp-of-the-perverse reblogged this · 2 weeks ago -
 matthew-the-imp-of-the-perverse liked this · 2 weeks ago
matthew-the-imp-of-the-perverse liked this · 2 weeks ago -
 backstreetmeat reblogged this · 2 weeks ago
backstreetmeat reblogged this · 2 weeks ago -
 backstreetmeat liked this · 2 weeks ago
backstreetmeat liked this · 2 weeks ago -
 dru-the-agender-god reblogged this · 2 weeks ago
dru-the-agender-god reblogged this · 2 weeks ago -
 dru-the-agender-god liked this · 2 weeks ago
dru-the-agender-god liked this · 2 weeks ago -
 rinkara reblogged this · 2 weeks ago
rinkara reblogged this · 2 weeks ago -
 morgan-aleghieri liked this · 2 weeks ago
morgan-aleghieri liked this · 2 weeks ago -
 falseapplication reblogged this · 2 weeks ago
falseapplication reblogged this · 2 weeks ago -
 zephonius reblogged this · 2 weeks ago
zephonius reblogged this · 2 weeks ago -
 quillpaw reblogged this · 2 weeks ago
quillpaw reblogged this · 2 weeks ago -
 tebbytime liked this · 2 weeks ago
tebbytime liked this · 2 weeks ago -
 brodyliciousbooty reblogged this · 2 weeks ago
brodyliciousbooty reblogged this · 2 weeks ago -
 brodyliciousbooty liked this · 2 weeks ago
brodyliciousbooty liked this · 2 weeks ago -
 tempest700 liked this · 2 weeks ago
tempest700 liked this · 2 weeks ago -
 narcicious reblogged this · 2 weeks ago
narcicious reblogged this · 2 weeks ago -
 lemonmeringuespy reblogged this · 2 weeks ago
lemonmeringuespy reblogged this · 2 weeks ago -
 ilovethetragicallybeautiful liked this · 2 weeks ago
ilovethetragicallybeautiful liked this · 2 weeks ago -
 l-infini-en-haut reblogged this · 2 weeks ago
l-infini-en-haut reblogged this · 2 weeks ago -
 goonssquadd reblogged this · 2 weeks ago
goonssquadd reblogged this · 2 weeks ago -
 bean-detritus reblogged this · 2 weeks ago
bean-detritus reblogged this · 2 weeks ago -
 sonohtigris reblogged this · 2 weeks ago
sonohtigris reblogged this · 2 weeks ago -
 caintooth liked this · 2 weeks ago
caintooth liked this · 2 weeks ago -
 felix-lupin reblogged this · 2 weeks ago
felix-lupin reblogged this · 2 weeks ago -
 idiotwithbinoculars liked this · 2 weeks ago
idiotwithbinoculars liked this · 2 weeks ago -
 janey-stempy liked this · 2 weeks ago
janey-stempy liked this · 2 weeks ago -
 noxboxsocks liked this · 2 weeks ago
noxboxsocks liked this · 2 weeks ago -
 bennetsandbridgertons reblogged this · 2 weeks ago
bennetsandbridgertons reblogged this · 2 weeks ago -
 pearlmaeiscool reblogged this · 2 weeks ago
pearlmaeiscool reblogged this · 2 weeks ago -
 definitelynotsorry reblogged this · 2 weeks ago
definitelynotsorry reblogged this · 2 weeks ago -
 definitelynotsorry liked this · 2 weeks ago
definitelynotsorry liked this · 2 weeks ago
